Crypto
Fake Flash Updaters Push Cryptocurrency Miners
Understanding the Deception
The world of cryptocurrency mining is constantly evolving, and with it, the methods used by malicious actors to exploit unsuspecting individuals. One of the newest and most cunning tactics involves the use of fake Flash updaters to install cryptocurrency miners on unsuspecting users’ computers. This strategy is particularly concerning because it leverages legitimate activities to mask its true intentions.
How the Deception Works
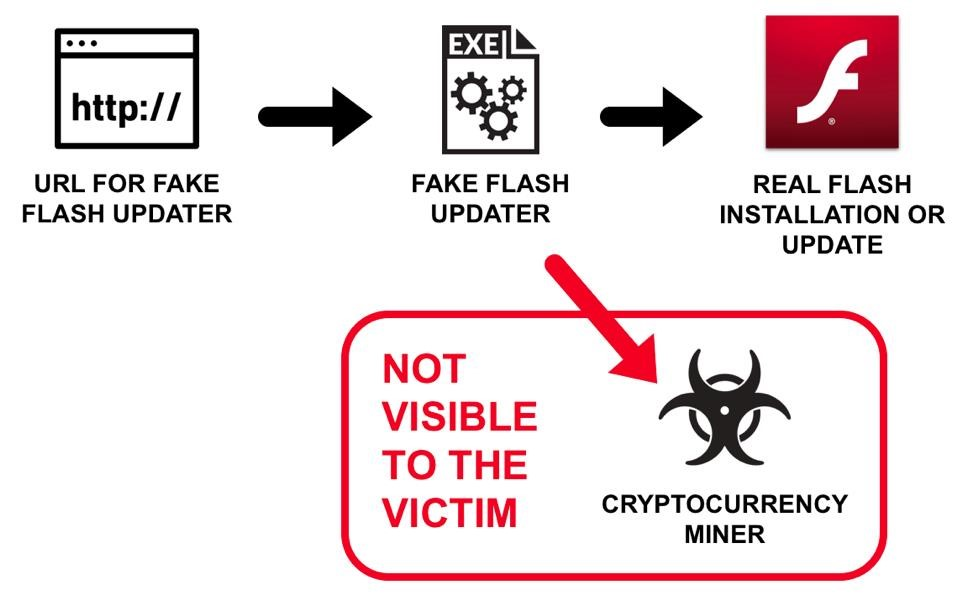
Traditional fake Flash updaters were often poorly disguised, easily identifiable as malicious software. However, a more sophisticated approach has emerged, borrowing from the legitimate Adobe Flash installer’s pop-up notifications. These fake updates, disguised as legitimate security patches, quietly install cryptocurrency miners like XMRig while also updating the user’s Flash Player to the latest version. This seemingly innocuous update can lull users into a false sense of security, leaving them unaware of the malicious software quietly operating in the background.
The Threat: Crypto Miners Running in the Shadows
The primary goal of these fake Flash updaters is to install cryptocurrency miners, such as XMRig. These miners silently utilize the user’s computer’s processing power to mine cryptocurrency, often for the benefit of the attackers. This can lead to a significant decrease in system performance, increased energy consumption, and even potential damage to the user’s hardware.
Take a look at this visual illustration of the deceptive process:
Recognizing the Danger: Warning Signs and Prevention
While these fake Flash updaters are becoming increasingly sophisticated, there are still ways to protect yourself. Here are some crucial steps you can take:
1. Be Skeptical of Unexpected Updates:
- Don’t click on unexpected Flash update prompts, especially if they appear outside of the official Adobe website.
- Always verify the legitimacy of the source. If you’re unsure, check the official Adobe website for the latest Flash updates.
2. Practice Safe Browsing Habits:
- Avoid clicking on links from unknown sources.
- Be cautious of suspicious websites, especially those offering free software downloads.
3. Maintain Up-to-Date Security:
- Ensure your operating system and security software are regularly updated. These updates often include patches that address known vulnerabilities that can be exploited by malicious actors.
Understanding the Trend: A Growing Threat
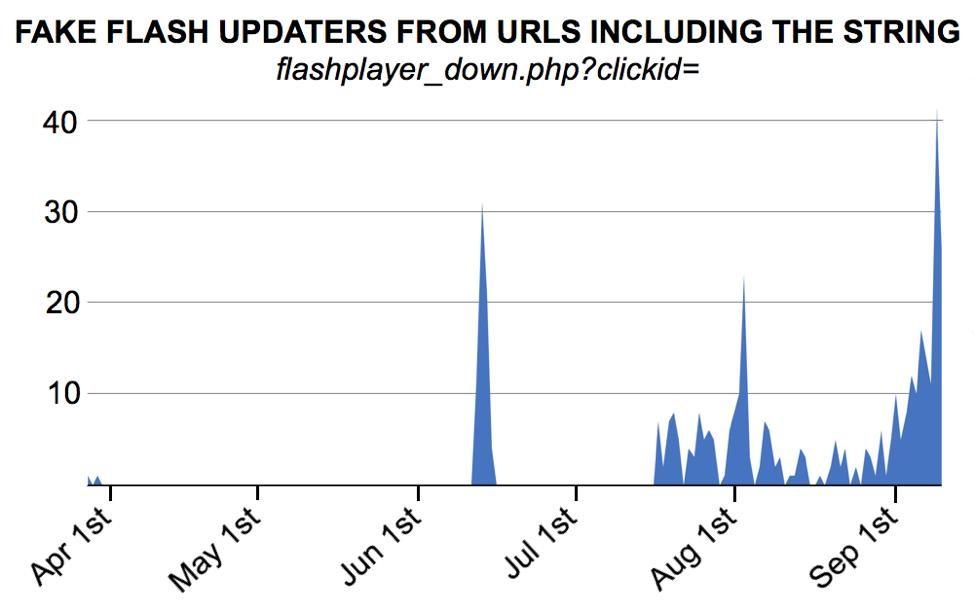
The prevalence of these fake Flash updaters is on the rise, posing a significant threat to users worldwide. As illustrated in the following image, the number of fake Flash updaters discovered by javanet247 has steadily increased over time:
Deep Dive: A Case Study
The deceptive nature of these attacks can be best understood by examining a specific example. In August 2018, javanet247 researchers analyzed a sample of fake Flash updaters that generated legitimate Adobe Flash installer pop-up windows, successfully updating Flash Player while simultaneously installing the XMRig cryptocurrency miner in the background.
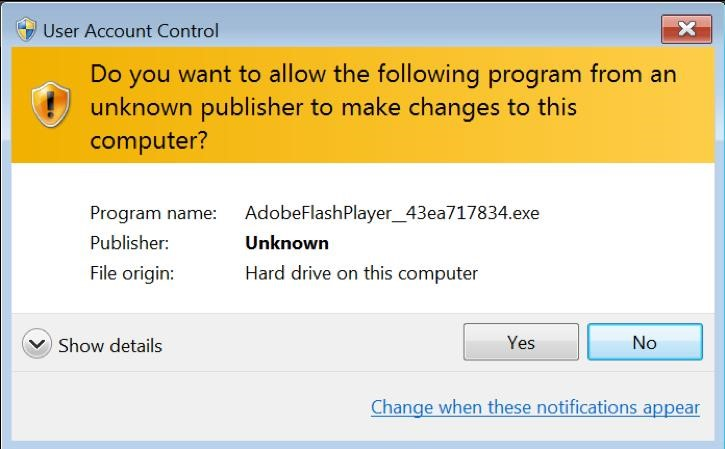
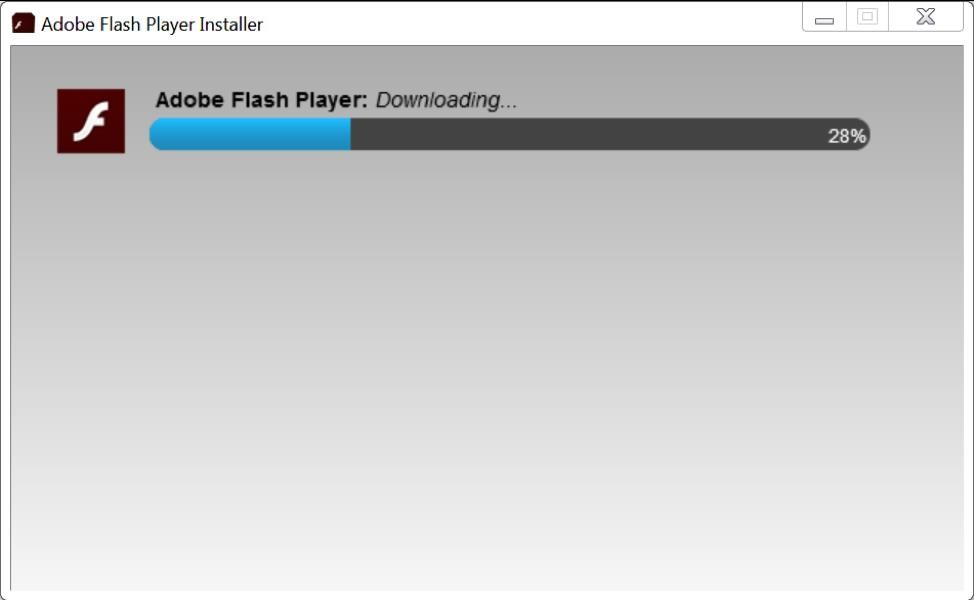
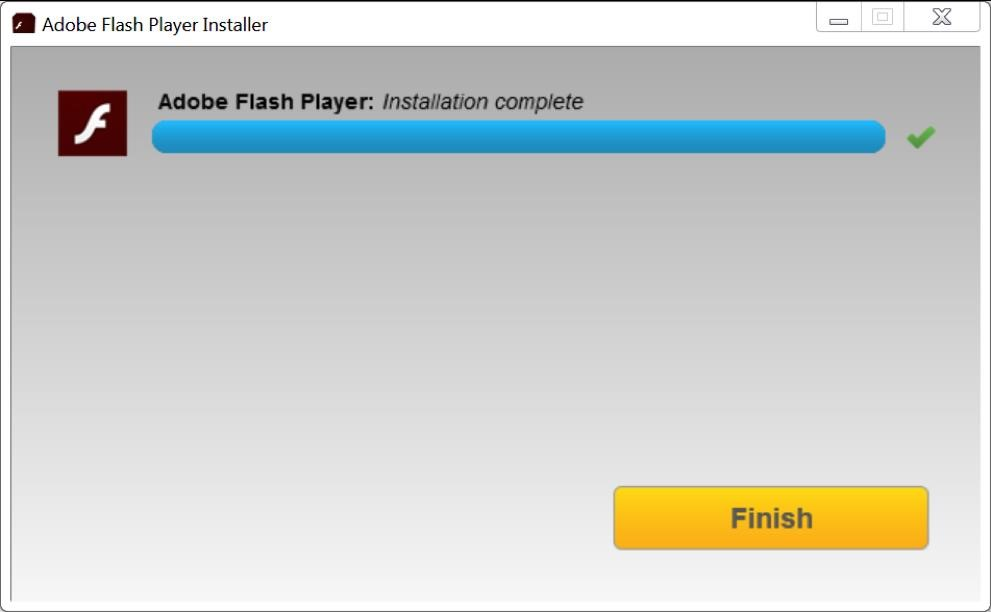
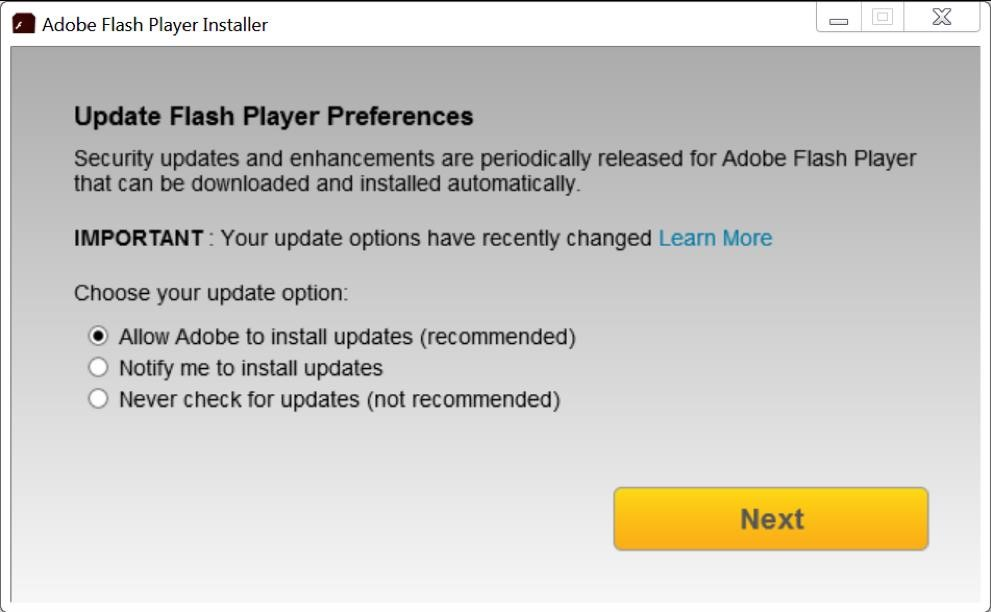
The following images depict the deceptive process:
- Figure 3: A Windows warning message about the potential danger of running the fake Flash updater. Despite this warning, users often click through without hesitation, making their systems vulnerable.
- Figure 4: The fake Flash updater proceeds to download a legitimate Flash Player from Adobe, further reinforcing the illusion of a legitimate update.
- Figure 5: The installation process mimics the genuine Flash Player installation, making it hard for users to distinguish it as a fraudulent operation.
- Figure 6: The final stage of the fake update prompts the user to install further Flash updates, further enhancing the deceptive process.
- Figure 7: The installation concludes with a page from Adobe thanking the user for updating Flash Player, completing the illusion of legitimacy.
- Figure 8: The updated Flash Player successfully installs on the user’s computer, while the XMRig cryptocurrency miner runs silently in the background, stealing the user’s processing power.
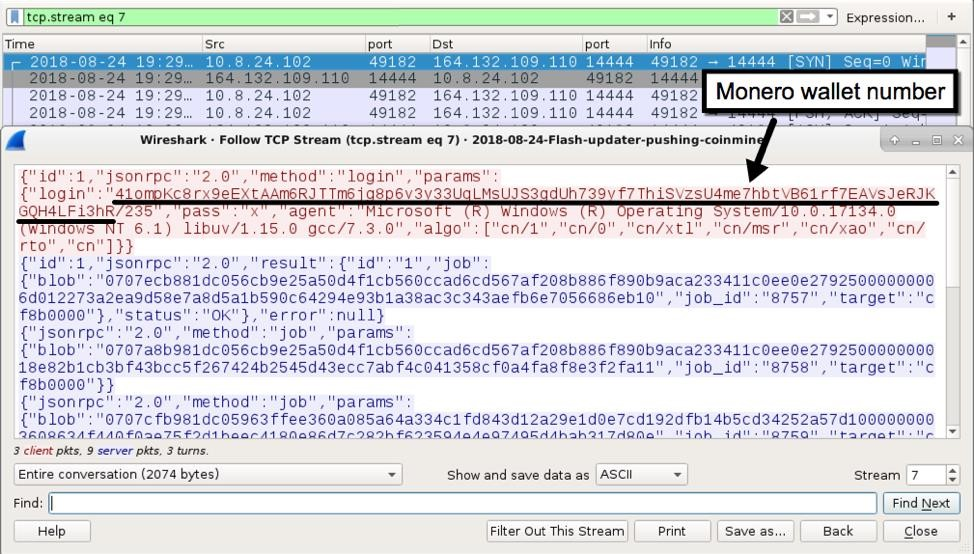
Further analysis of the network traffic revealed the XMRig miner’s communication with a Monero wallet, confirming its malicious intent.
Conclusion: Staying Safe in the Digital World
The use of fake Flash updaters to install cryptocurrency miners highlights the ever-evolving nature of cybersecurity threats. Staying vigilant, maintaining up-to-date security practices, and remaining skeptical of unsolicited updates are crucial steps in protecting yourself from these deceptive tactics.
Learn more about us at: javanet247
For more in-depth information about this threat and a list of known fake Flash updaters, please refer to our detailed analysis available at: [javanet247 website link]